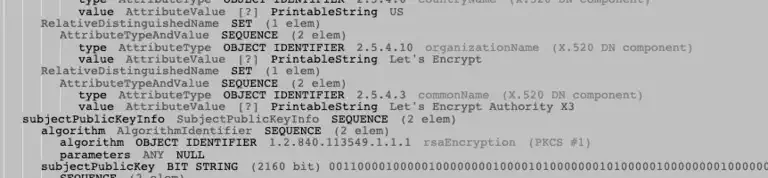
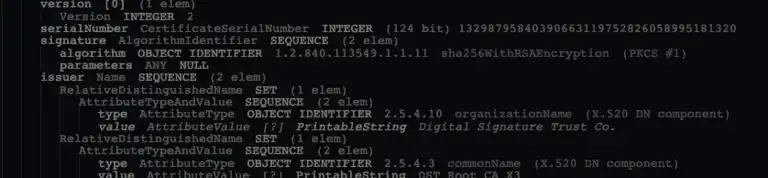
For certificates to work, we need a system of trust. We need to know that each certificate is valid and was properly issued. This is the role of the certificate authorities (CAs). In the second part of this series, we’ll explore the role of CAs and how certificates are validated. We’ll also look at creating a private CA using a self-signed certificate.

Ken Muse