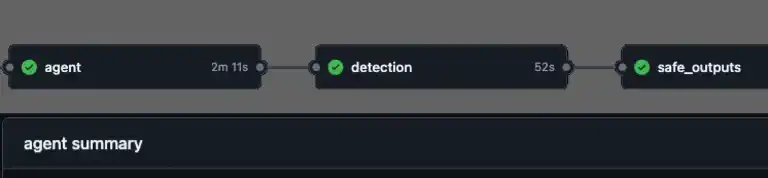
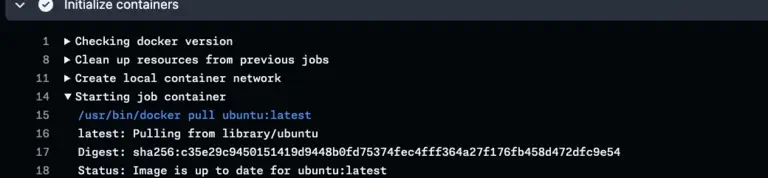
What if your repository could triage issues, investigate CI failures, and update documentation without you? GitHub just launched Agentic Workflows – a new way to automate repository tasks using AI coding agents, all written in plain Markdown. Here’s a look at how they work, what makes the security model interesting if you work with AI, and why you should pay attention.

Ken Muse