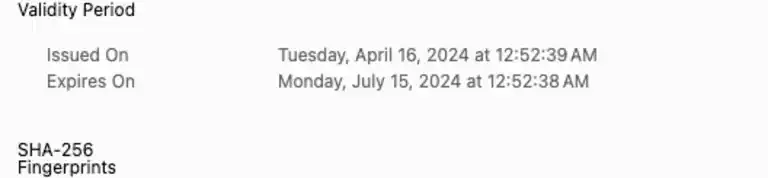
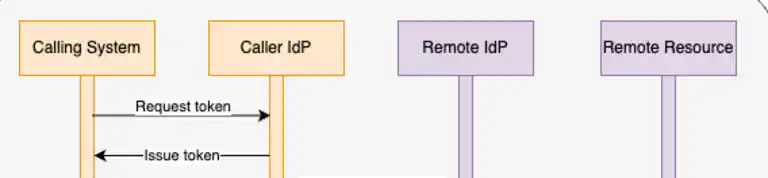
Do you know what the main threat is to your CI/CD systems? It’s not the code you write, the tools you use, or the cloud provider you rely on. It’s the supply chain, and that is frequently the most vulnerable part of the development process. Today, let’s understand why.

Ken Muse