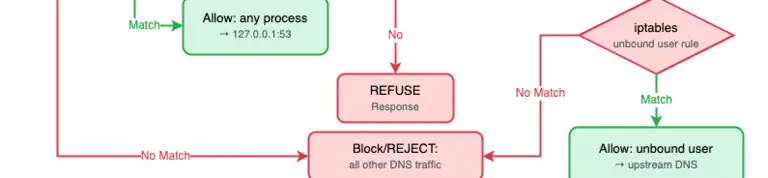
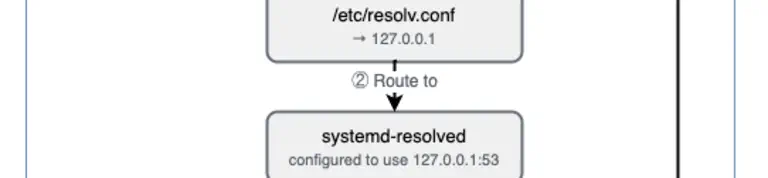
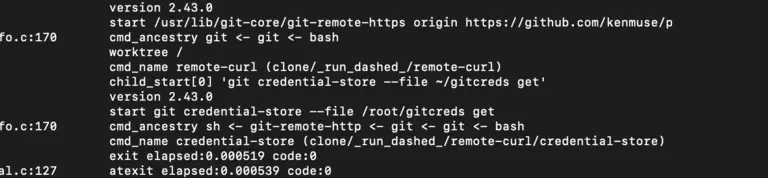
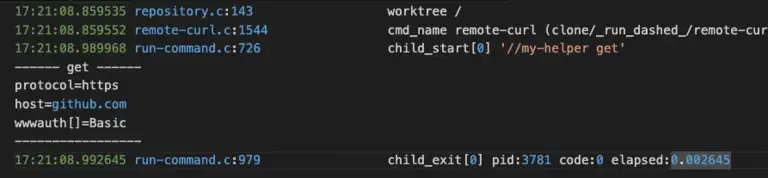
When the Shai-Hulud v2 supply chain attack hit last week, I watched thousands of developers scramble to check their systems. Mine? I was able to mark it as safe. This was because I’d already layered in some straightforward security practices. If you’re wondering how to protect your own development environment from these kinds of attacks, I’ll walk you through the exact configurations and tools I use every day that kept me safe.

Ken Muse